Single sign on (SSO) setup
Simon supports Single Sign On (SSO) for all organizations. Simon supports any SAML-based Identity Provider (IdP), including Okta, One Login, or Microsoft Azure to serve as your identity provider, delegating access to the application based on rules you create in your central identity management solution.
Pro-TipSSO provides an additional layer of protection for your organization's user accounts. With application access granted through SAML there are no passwords for your organization's users for the application that can be compromised.
Configuration Procedure
Configuring SSO is a three part process:
1. Configure in Your Identity Provider
To configure in your identity provider, see both their documentation and also the following example sections. Some commonly used providers are:
2. Configure in Simon
Once the application is created in your identity provider, an admin user in Simon Data can fill in the necessary SSO fields:
- From your profile drop down, click Settings
- Under Security, click Authentication.
- Toggle Single-Sign On to on.
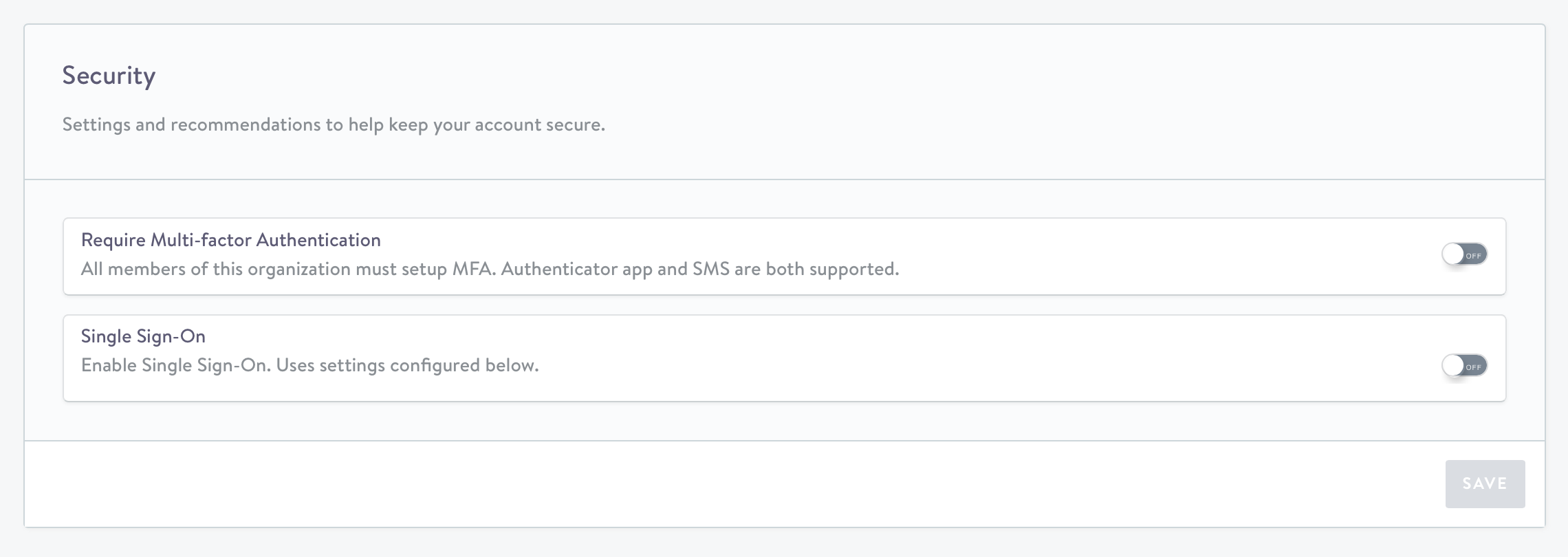
- Complete the Entity ID, Single Signon URL, Single Logout URL (optional), and 509 Certificate.
- Click Save.
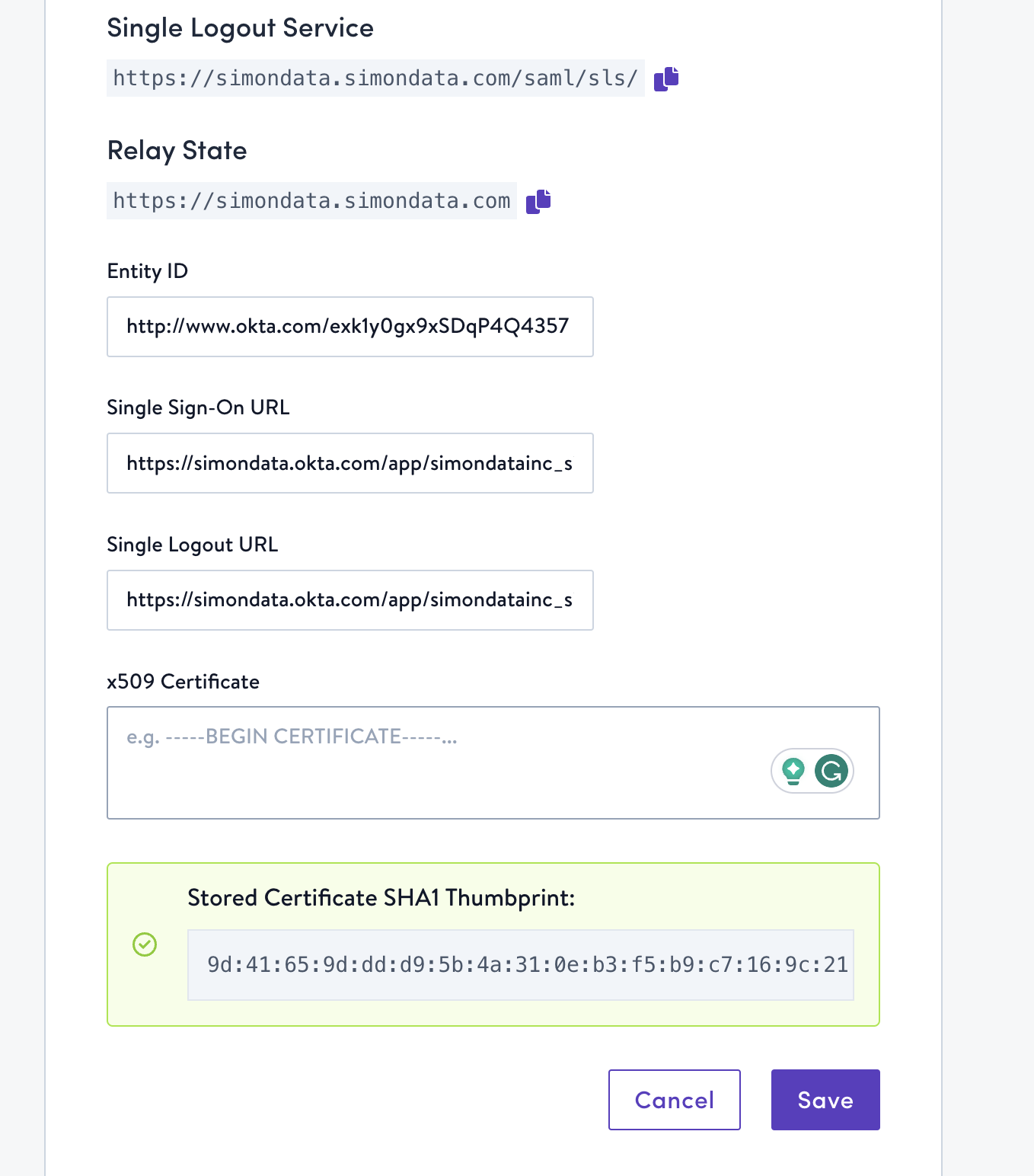
The values to include in each field depend on your identity provider. Find your provider's section below for more specific details. If you don't see your provider listed and need assistance, contact your account manager.
3. Roll out
Simon Data allows for multiple authentication options, and optionally supports limiting authentication only to SSO users. Once SSO is working as expected, you can reach out to your client solutions manager to turn off password-based login.
Example Okta SAML Application Configuration
Review Okta's documentation. Please note, identity provider documentation URLs can change.
Configure in Simon Data
| Field | Value |
|---|---|
| Entity ID | http://www.okta.com/abcde12345 |
| Single Signon URL | https://YOUR-COMPANY.okta.com/app/companyname_appname/abcde12345/sso/saml |
| Single Logout URL | https://YOUR-COMPANY.okta.com/app/companyname_appname/abcde12345/slo/saml |
| X509 Certificate | -----BEGIN CERTIFICATE----- ... -----END CERTIFICATE----- (Paste with line returns, no \n) |
Configure in Okta
| Field | Value |
|---|---|
| Single Sign On URL | https://<organization-name>.simondata.com/saml/acs/ |
| Recipient URL | https://<organization-name>.simondata.com/saml/acs/ |
| Destination URL | https://<organization-name>.simondata.com/saml/acs/ |
| Audience Restriction | https://<organization-name>.simondata.com/saml/metadata/ Note: the trailing / is required. |
| Default Relay State | https://<organization-name>.simondata.com |
| Single Logout (optional) | https://<organization-name>.simondata.com/saml/sls/ |
| NameID | EmailAddress |
| Additional Attributes (optional) | FirstName = user.firstNameLastName = user.lastName |
| Other Settings (defaults) | Assertion: signedResponse: signedSignature Algorithm: RSA_SHA256Digest Algorithm: SHA256 |
Example Azure AD SAML Configuration
Review Microsoft's documentation. Please note, identity provider documentation URLs can change.
Configure in Simon Data
| Field | Value |
|---|---|
| Entity ID | https://sts.windows.net/4567abcd-1234/ |
| Single Signon URL | https://login.microsoftonline.com/44444-0000-9999-cccc-abcde1234/saml2 |
| Single Logout URL | https://login.microsoftonline.com/common/wsfederation?wa=wsignout1.0 |
| X509 Certificate | -----BEGIN CERTIFICATE----- ... -----END CERTIFICATE----- (Paste with line returns, no \n) |
Configure in Azure AD
| Field | Value |
|---|---|
| Identifier / Entity | https://<organization-name>.simondata.com/saml/metadata/ |
| Reply URL | https://<organization-name>.simondata.com/saml/acs/ |
| Signon URL | https://<organization-name>.simondata.com/saml/sso/ |
| Relay State (optional) | https://<organization-name>.simondata.com/ |
| Logout URL (optional) | https://<organization-name>.simondata.com/saml/sls/ |
| Name Identifier Value | user.mail (typical) |
| Additional Attributes | FirstName = user.givennameLastName = user.surname |
Example ADFS SAML 2.0 Configuration
We recommend reviewing the documentation for configuring a SAML application for your exact version of ADFS. You may find the screenshots of setup with other applications helpful, such as this one: Confluence ADFS SAML setup
Configure in Simon Data
| Field | Value |
|---|---|
| Entity ID | http://adfs/<FEDERATION_SERVICE_ID>/trust |
| Single Signon URL | https://<myadfsserver.com>/adfs/ls/ |
| X509 Certificate | -----BEGIN CERTIFICATE----- ... -----END CERTIFICATE----- (Export with Base64 encoding. Paste with line returns, no \n) |
Configure in ADFS
XML Configuration: https://<organization-name>.simondata.com/saml/metadata/
| Configuration | Value |
|---|---|
| Relying party SAML 2.0 SSO Service URL | https://<organization-name>.simondata.com/saml/acs/ |
| Relying party trust identifier | https://<organization-name>.simondata.com/saml/metadata/ |
| Name ID | email address |
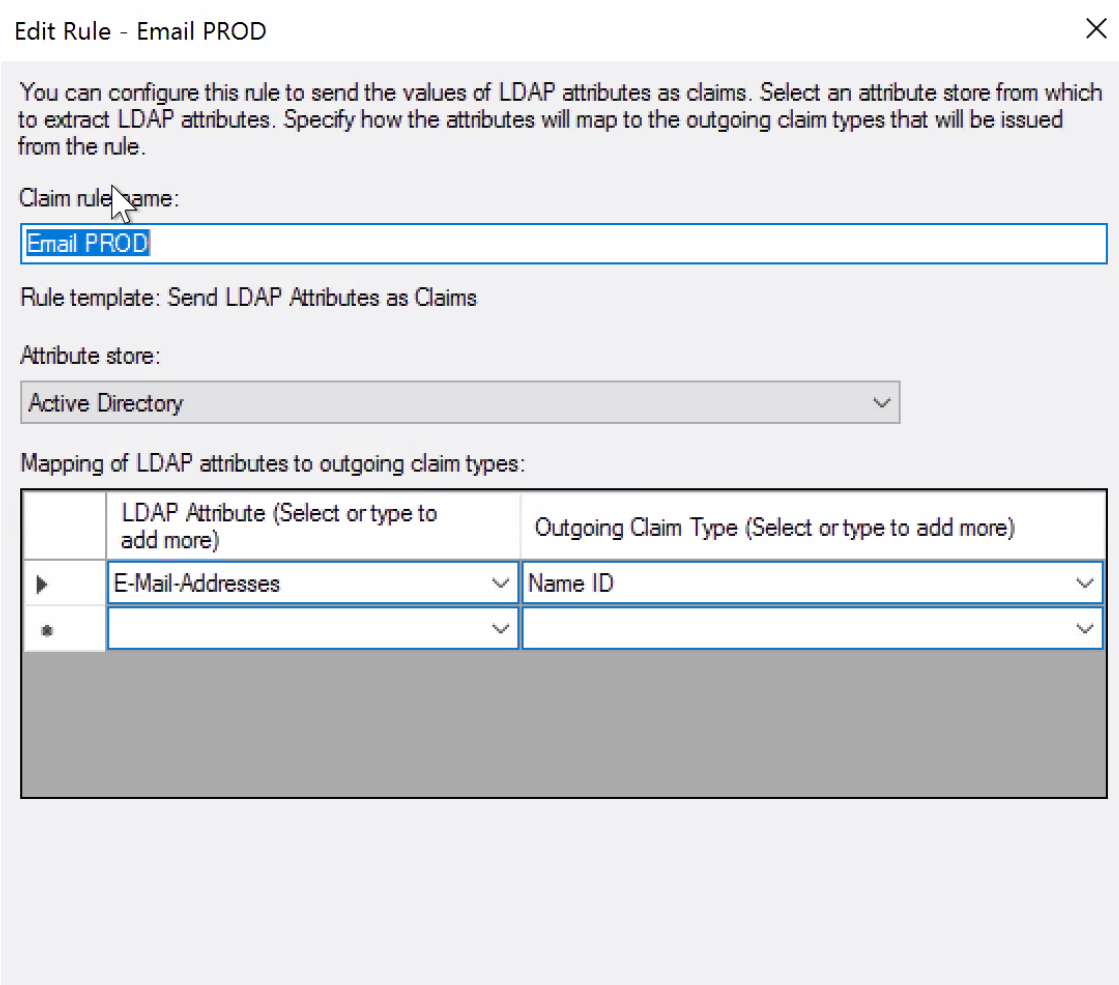
| Example Name Identifier Custom Rule | c:[Type == "http://schemas.xmlsoap.org/ws/2005/05/identity/claims/emailaddress"] => issue(Type = "http://schemas.xmlsoap.org/ws/2005/05/identity/claims/nameidentifier", Issuer = c.Issuer, OriginalIssuer = c.OriginalIssuer, Value = c.Value, ValueType = c.ValueType, Properties["http://schemas.xmlsoap.org/ws/2005/05/identity/claimproperties/format"] = "urn:oasis:names:tc:SAML:1.1:nameid-format:emailAddress"); |
Example NameID Claim Rule:
Updated 3 months ago
